Keycloak (in Docker Swarm)
Keycloak is "an open source identity and access management solution". Using a local database, or a variety of backends (think OpenLDAP), you can provide Single Sign-On (SSO) using OpenID, OAuth 2.0, and SAML.
Keycloak's OpenID provider can also be used in combination with Traefik Forward Auth, to protect vulnerable services with an extra layer of authentication.
Keycloak Requirements
Ingredients
Already deployed:
- Docker swarm cluster with persistent shared storage
- Traefik configured per design
- DNS entry for the hostname you intend to use (or a wildcard), pointed to your keepalived IP
Related:
- Traefik Forward Auth or Authelia to secure your Traefik-exposed services with an additional layer of authentication
Setup
Keycloak filesystem paths
We'll need several directories to bind-mount into our container for both runtime and backup data, so create them as per the following example:
mkdir -p /var/data/runtime/keycloak/database
mkdir -p /var/data/keycloak/database-dump
Keycloak environment vars
Create /var/data/config/keycloak/keycloak.env, and populate with the following example variables, customized for your own domain structure.
# Technically, this could be auto-detected, but we prefer to be prescriptive
DB_VENDOR=postgres
DB_DATABASE=keycloak
DB_ADDR=keycloak-db
DB_USER=keycloak
DB_PASSWORD=myuberpassword
KEYCLOAK_USER=admin
KEYCLOAK_PASSWORD=ilovepasswords
# This is required to run keycloak behind traefik
PROXY_ADDRESS_FORWARDING=true
# What's our hostname?
KEYCLOAK_HOSTNAME=keycloak.example.com
# Tell Postgress what user/password to create
POSTGRES_USER=keycloak
POSTGRES_PASSWORD=myuberpassword
Create /var/data/config/keycloak/keycloak-backup.env, and populate with the following, so that your database can be backed up to the filesystem, daily:
PGHOST=keycloak-db
PGUSER=keycloak
PGPASSWORD=myuberpassword
BACKUP_NUM_KEEP=7
BACKUP_FREQUENCY=1d
Docker compose example
Create a Keycloak docker-compose (v3) stack config file, something like this example:
Fast-track with premix! 🚀
"Premix" is a git repository which includes necessary docker-compose and env files for all published recipes. This means that you can launch any recipe with just a git pull and a docker stack deploy 👍.
🚀 Update: Premix now includes an ansible playbook, enabling you to deploy an entire stack + recipes, with a single ansible command! (more here)
version: '3'
services:
keycloak:
image: jboss/keycloak
env_file: /var/data/config/keycloak/keycloak.env
volumes:
- /etc/localtime:/etc/localtime:ro
networks:
- traefik_public
- internal
deploy:
labels:
# traefik
- traefik.enable=true
- traefik.docker.network=traefik_public
# traefikv1
- traefik.frontend.rule=Host:keycloak.example.com
- traefik.port=8080
# traefikv2
- "traefik.http.routers.keycloak.rule=Host(`keycloak.example.com`)"
- "traefik.http.routers.keycloak.entrypoints=https"
- "traefik.http.services.keycloak.loadbalancer.server.port=8080"
keycloak-db:
env_file: /var/data/config/keycloak/keycloak.env
image: postgres:10.1
volumes:
- /var/data/runtime/keycloak/database:/var/lib/postgresql/data
- /etc/localtime:/etc/localtime:ro
networks:
- internal
keycloak-db-backup:
image: postgres:10.1
env_file: /var/data/config/keycloak/keycloak-backup.env
volumes:
- /var/data/keycloak/database-dump:/dump
- /etc/localtime:/etc/localtime:ro
entrypoint: |
bash -c 'bash -s <<EOF
trap "break;exit" SIGHUP SIGINT SIGTERM
sleep 2m
while /bin/true; do
pg_dump -Fc > /dump/dump_\`date +%d-%m-%Y"_"%H_%M_%S\`.psql
(ls -t /dump/dump*.psql|head -n $$BACKUP_NUM_KEEP;ls /dump/dump*.psql)|sort|uniq -u|xargs rm -- {}
sleep $$BACKUP_FREQUENCY
done
EOF'
networks:
- internal
networks:
traefik_public:
external: true
internal:
driver: overlay
ipam:
config:
- subnet: 172.16.49.0/24
Note
Setup unique static subnets for every stack you deploy. This avoids IP/gateway conflicts which can otherwise occur when you're creating/removing stacks a lot. See my list here.
Run Keycloak
Launch Keycloak docker-swarm stack
Launch the Keycloak stack by running docker stack deploy keycloak -c <path -to-docker-compose.yml>
Log into your new instance at https://YOUR-FQDN, and login with the user/password you defined in keycloak.env.
Create Keycloak user
Why are we adding a user when I have an admin user already?
Do you keep a spare set of house keys somewhere other than your house? Do you login as root onto all your systems? Think of this as the same prinicple - lock the literal admin account away somewhere as a "password of last resort", and create a new user for your day-to-day interaction with Keycloak.
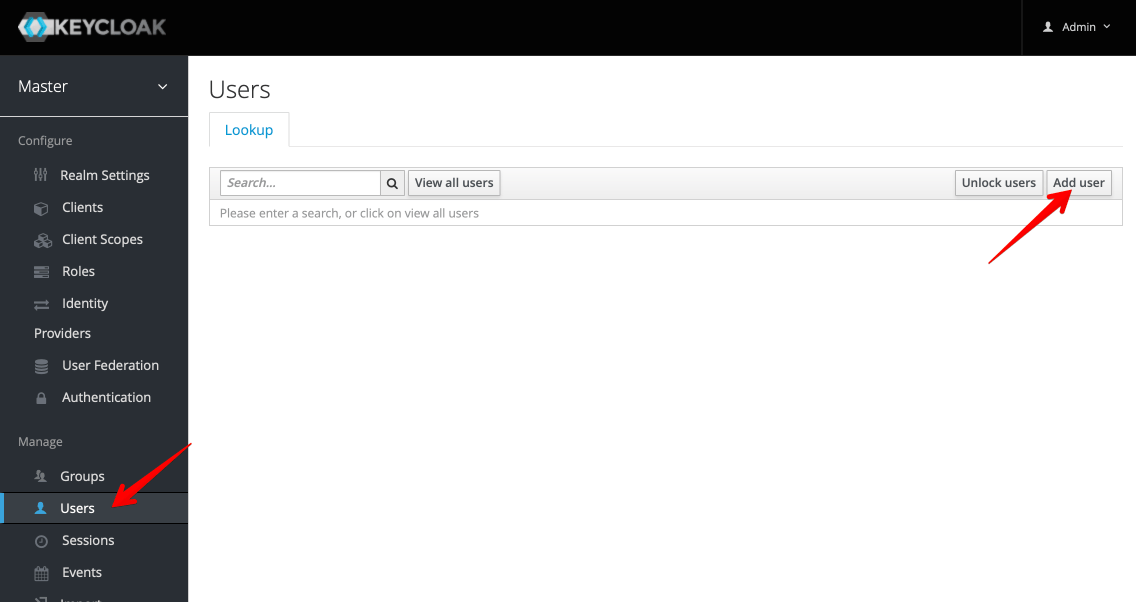
Within the "Master" realm (no need for more realms yet), navigate to Manage -> Users, and then click Add User at the top right:
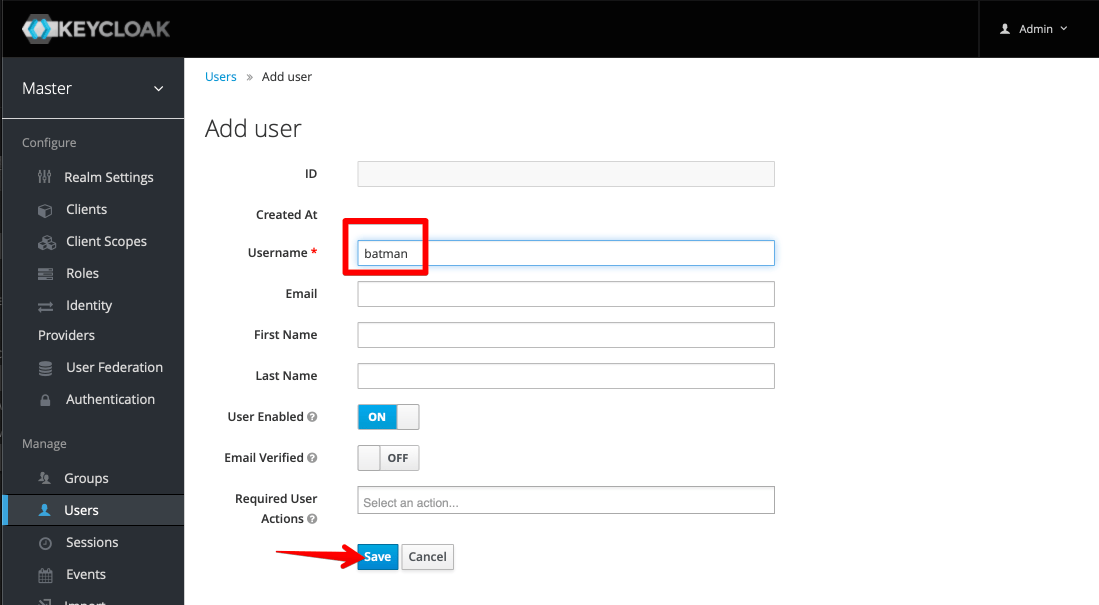
Populate your new user's username (it's the only mandatory field)
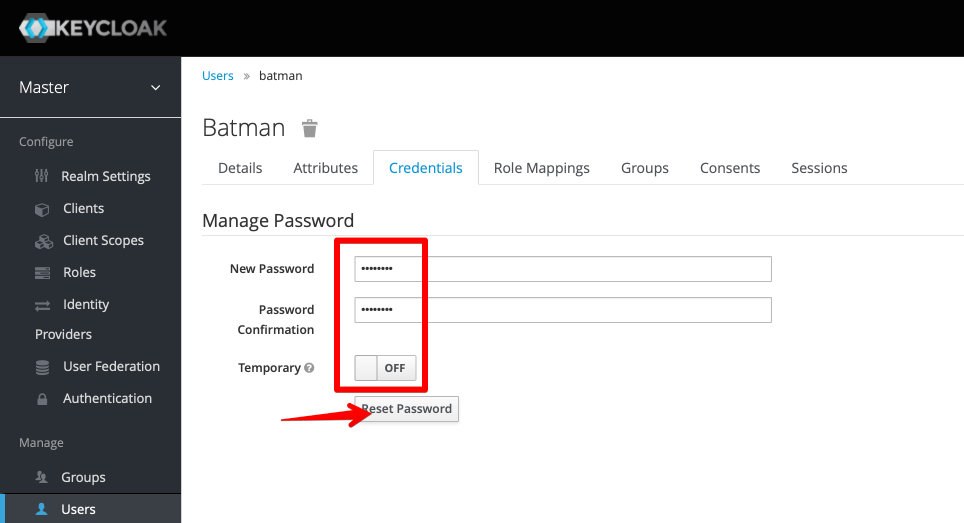
Set Keycloak user credentials
Once your user is created, to set their password, click on the "Credentials" tab, and procede to reset it. Set the password to non-temporary, unless you like extra work!
Tips
Keycloak with Traefik
Keycloak can be used with Traefik in two ways..
Keycloak behind Traefik
You'll notice that the docker compose example above includes labels for both Traefik v2 and Traefik v2. You obviously don't need both (although it wont't hurt), but make sure you update the example domain in the Traefik labels. Keycloak should work behind Traefik without any further customization.
Keycloak as Traefik middleware
Irrespective of whether Keycloak itself is behind Traefik, you can secure access to other services behind Traefik using Keycloak, using the Traefik Forward Auth middleware. Other similar middleware solutions are traefik-gatekeeper, and oauth2-proxy.
Keycloak Troubleshooting
Something didn't work? Try the following:
- Confirm that Keycloak did, in fact, start, by looking at the state of the stack, with
docker stack ps keycloak --no-trunc
Chef's notes 📓
Tip your waiter (sponsor) 👏
Did you receive excellent service? Want to compliment the chef? (..and support development of current and future recipes!) Sponsor me on Github / Ko-Fi / Patreon, or see the contribute page for more (free or paid) ways to say thank you! 👏
Employ your chef (engage) 🤝
Is this too much of a geeky PITA? Do you just want results, stat? I do this for a living - I'm a full-time Kubernetes contractor, providing consulting and engineering expertise to businesses needing short-term, short-notice support in the cloud-native space, including AWS/Azure/GKE, Kubernetes, CI/CD and automation.
Learn more about working with me here.
Flirt with waiter (subscribe) 💌
Want to know now when this recipe gets updated, or when future recipes are added? Subscribe to the RSS feed, or leave your email address below, and we'll keep you updated.